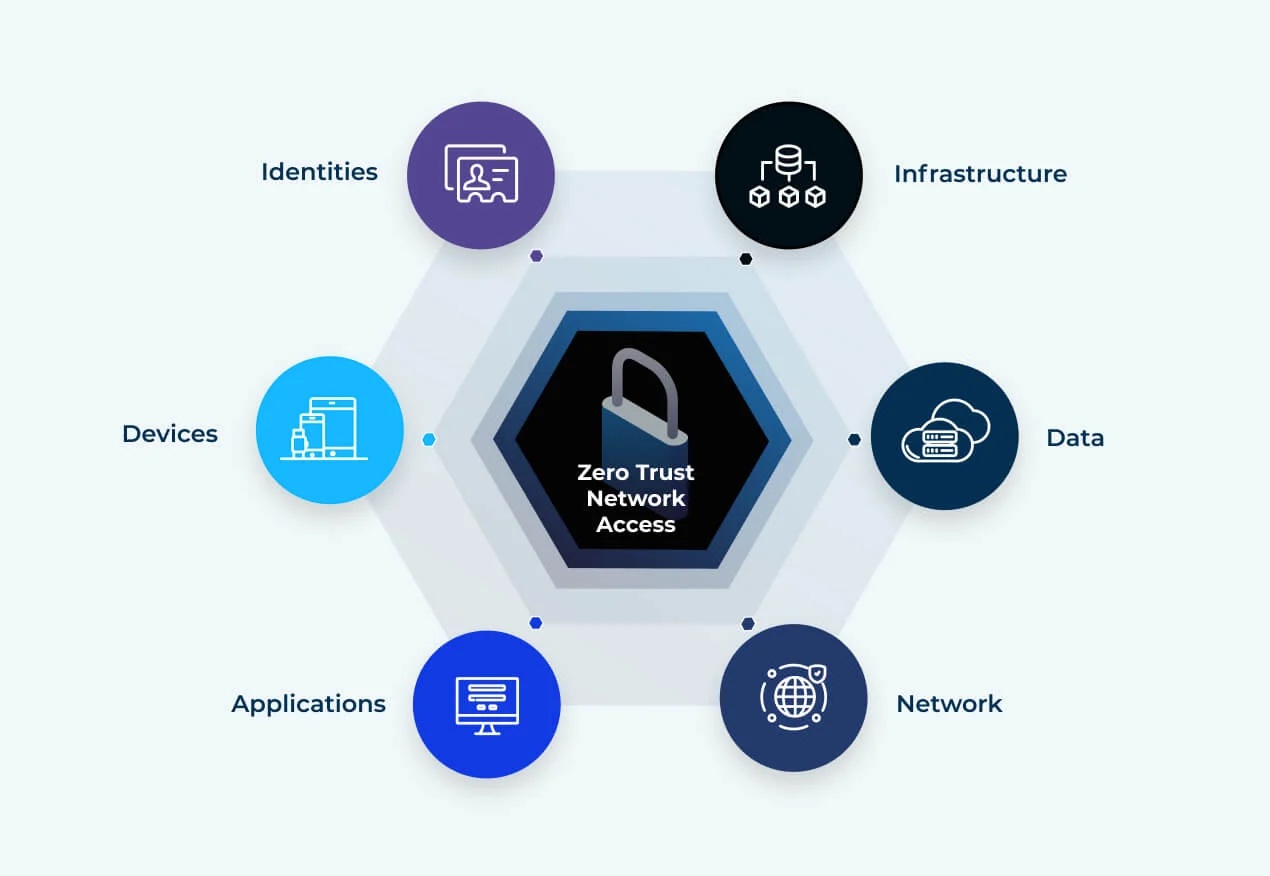
Designing a Zero Trust Apple Device Architecture
The concept of “trust no one, verify everything” has moved from cybersecurity buzzword to business imperative. For organizations managing Apple…
Recent Post
- Designing a Zero Trust Apple Device Architecture
- Bridging Windows and macOS: Enterprise Identity Integration Strategies
- Beginner Guide: Apple Intelligence in Enterprise – Privacy Architecture and MDM Control Mechanisms
- Deep Dive: Understanding Declarative Device Management – The Future of Apple MDM
- Apple Native Virtualization: The Enterprise Guide to Built-In VM Capabilities
Enterprise Mobility & EUC
Comparison: Workspace ONE Access Cloud vs. On-Prem
Introduction: The Identity Management Crossroads As organizations increasingly embrace digital transformation, the…
Comparison: Workspace ONE UEM Cloud vs. On-Prem
Introduction: The UEM Deployment Dilemma As organizations increasingly adopt Unified Endpoint Management…
Use Case: Why a Financial Firm Chose On-Prem VDI with VMware Horizon Over DaaS
Introduction: The Cloud-First Dilemma In today’s IT landscape, “cloud-first” has become a…
Apple
Apple Native Virtualization: The Enterprise Guide to Built-In VM Capabilities
When Apple introduced the Virtualization framework in macOS Big Sur alongside the launch of Apple Silicon, it fundamentally transformed how…
Beginner Guide: Apple Intelligence in Enterprise – Privacy Architecture and MDM Control Mechanisms
When Apple Intelligence launched across iOS 18, iPadOS 18, and macOS 15, it brought enterprise IT teams a new challenge:…
Security & Identity
Comparison: Workspace ONE Access Cloud vs. On-Prem
Introduction: The Identity Management Crossroads As organizations increasingly embrace digital transformation, the…
Deep Dive: Workspace ONE Cloud – What Data Actually Exposed
Introduction: Understanding Data Exposure in Cloud UEM As organizations increasingly adopt cloud-based…
Implementation Guide: Configuring Okta as a Third-Party Identity Provider for Workspace ONE
Introduction: Bridging Identity Management Systems As organizations adopt multi-cloud strategies and diverse…
AI & Automations
Deep Dive: Retrieval-Augmented Generation (RAG) for Enterprise Chatbots
Introduction After implementing Retrieval-Augmented Generation (RAG) systems for enterprise chatbots…
Implementation Guide: Building Private AI Infrastructure with NVIDIA AI Enterprise
Introduction After architecting private AI infrastructure solutions for dozens of…
Cloud Computing
Implementation Guide: Automating VM Deployments with Terraform and vSphere
Introduction: Infrastructure as Code Meets Virtualization In my years of…