Designing a Zero Trust Apple Device Architecture
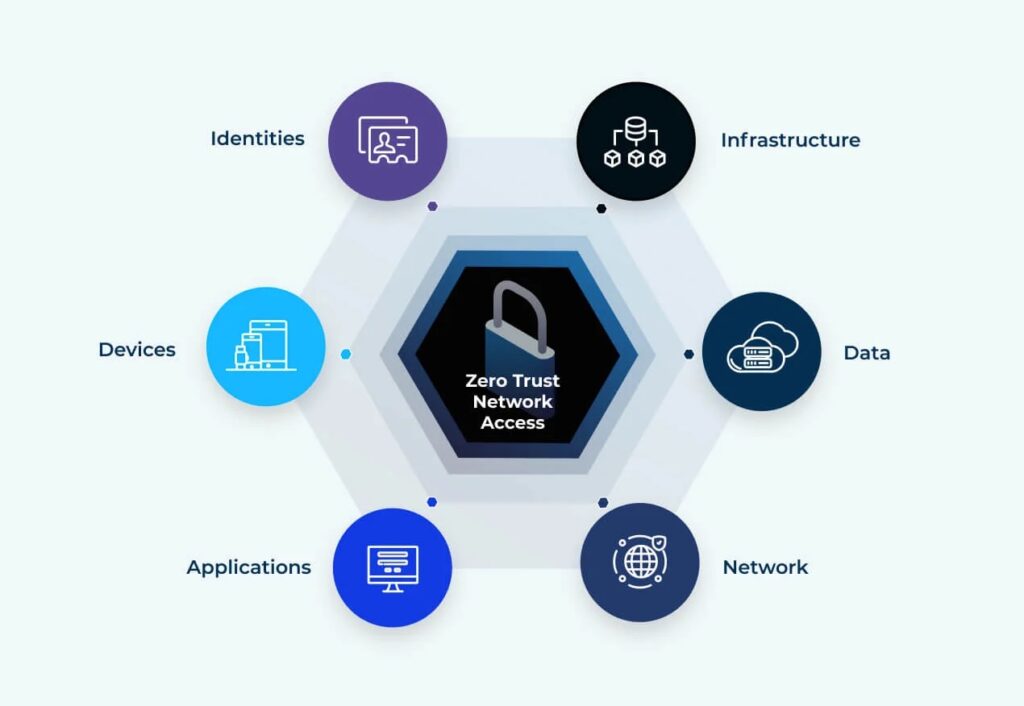
The concept of “trust no one, verify everything” has moved from cybersecurity buzzword to business imperative. For organizations managing Apple devices at scale, implementing Zero Trust isn’t just about checking compliance boxes—it’s about fundamentally rethinking how devices, users, and data interact across your enterprise. I’ve spent considerable time working with organizations transitioning their Apple device […]
Designing a Zero Trust Apple Device Architecture Read More »